Our article “The Compensation Trap” has been published on ISACA Journal. The article explains “Why Less cyber security staff is More”
Categorie: Blogs
Yuri Bobbert on SAI Belgium Podcast
The Compensation Trap – Why Less cyber security staff is More
Introduction Security departments are growing out of their seams. While demand for cyber security professionals is growing, finding and retaining good staff takes hard work. According to the 2022 (ISC)2, Cybersecurity Workforce Study 1, about 70% of respondents said their organizations don’t have enough cybersecurity employees. And while the number of professionals is growing, security is not at its required levels yet. Are we utilizing our resources wisely? If so, you can
Influential trends for emerging roles in digital security – 2023 and beyond
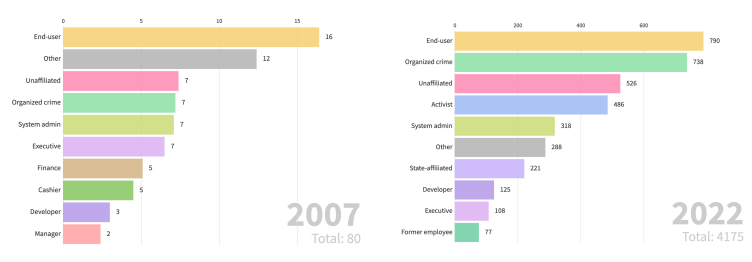
By Yuri Bobbert and Vincent van Dijk Looking at cyberdata collected in recent times reveals intriguing insights that may affect our future view on digital security education as a prime defense mechanism for dealing with future threats. In this article, we first observe the cumulative change in cyber threat actors followed by summarizing our analysis of more than 20 years of cyberdata, based on the VERIS Community Database in order to
Yuri Bobbert in Belgium media about five future digital security roles
Belgium media Metro and IT Daily published an article of Yuri Bobbert about five future digital security roles that is based upon the book “Leading in Digital Security – twelve ways to combat the silent enemy“. You can find the Metro article in French here. The IT Daily article can be found in Dutch here
Yuri Bobbert guest at the V-ICT-OR Podcast
Five things Digital Security Leaders can learn from Elon Musks Twitter takeover
First of all, we don’t drive a Tesla and are not Elon Musk fans. However, we do think that the recent developments since Elon Musk took over Twitter bring some interesting insights and learnings. Where multiple people coin Elon Musk as a poor leader, we tend to believe differently and share a different perspective. At the moment of writing this blog, Elon Musk just decided to step down as Twitter
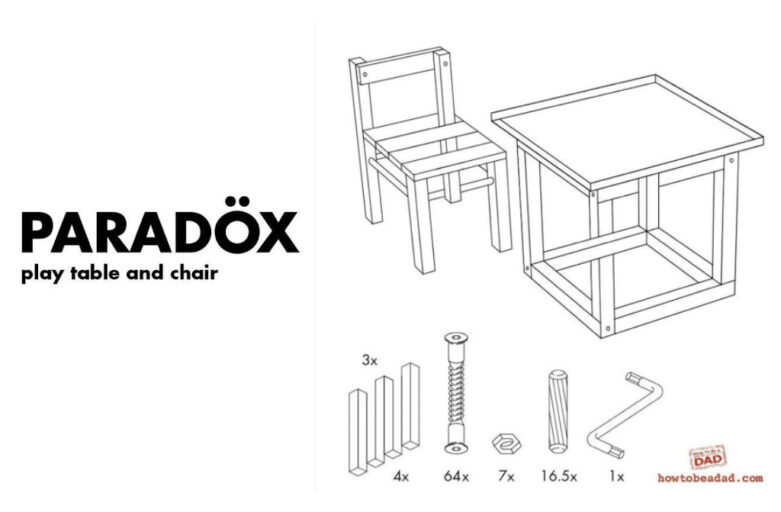
The IKEA effect on Cybersecurity investment decisions
Have you ever been to an IKEA store? Then you are perhaps already familiar with the satisfying effect of assembling and building stuff yourself. The IKEA effect has been investigated extensively in behavioral and decision sciences. But what does it tell us, and how does it help us with better cybersecurity investment decisions in the long term? What can we learn from the IKEA effect, and how does it help
Why Security Awareness Campaigns aren’t enough for secure behavior
How to create an attitude of “I have to” towards “I want to.” It’s October again, and this means it’s security awareness month! This month, we hang posters, give away some goodies, do hackathons, do hack competitions, and probably do some security awareness training. All good, but does it change people to behave more securely “aware”? Why do some of us -still- drive too fast We all know that driving
Yuri Bobbert guest at the Podcast “Change Dynamics”
Yuri Bobbert was recently a guest in the Podcast Change Dynamics. Listen to Episode #9 “Zero Trust requires another way of thinking” where Yuri talks about the book “Leading in Digital Security” and related topics like: Cultural Change, Leadership, CISO Archetypes, Craftmanship, Design Science Research and Zero Trust as a Service. Listen to the podcast here, on Spotify or Apple Podcast.