How to create an attitude of “I have to” towards “I want to.”
It’s October again, and this means it’s security awareness month! This month, we hang posters, give away some goodies, do hackathons, do hack competitions, and probably do some security awareness training. All good, but does it change people to behave more securely “aware”?
Why do some of us -still- drive too fast
We all know that driving too fast is dangerous and not allowed. But still, hundreds of people do it. They operate on the speed limit when they see police or trajectory control. Are these people criminals, idiots, or do they just not see the need to change their behavior because the government tells them? The reason why we shouldn’t drive too fast is because of safety. Moving fast increases the risk of getting yourself or others injured or killed in a crash. That makes sense, but why do many of us still exceed the speed limit?
If you look at it from another perspective, there could be several reasons this rule might no longer be valid. Cars have become much safer and more responsive, limiting the risk of injury or death. Some people can drive a car very well; others just don’t, so why should those great drivers follow the rules for the slow ones? In some cases, we even see police cars, which should give a good example, driving too fast without sirens or actual urgency. In many European countries, highway speed is also regulated due to nitrogen emissions. This rule applies not only to diesel or gasoline cars but also to battery and hydrogen cars.
Whether you agree with it or not, it does make sense that some people don’t agree with speed limits and only adhere to them when they can get caught. In some cases, they will comply temporarily after receiving a hefty fine, but that impulse will vanish after some time. Also, putting more billboards next to the road to make them aware not to exceed speed limits will probably not change their way of driving, or will they?
Why only Awareness training doesn’t change our behavior
So, what is the actual trigger for people to change their behavior? We think the intrinsic motivation to change people’s behavior is much more complex than just awareness campaigns with posters. Two interesting studies, which we also highlight in our book Leading in Digital Security, reveal to us how we can do better:
The first one is the Kübler-Ross change curve[1], which clarifies that everyone goes through different stages of grief when something needs to change. The origin of this curve is the 5-stages of grief a person goes through after a loved one passes away. These 5-stages are denial, anger, bargaining, depression, and acceptance. This curve also appeared valuable in the corporate world to understand the emotional status of an employee when going through a change.
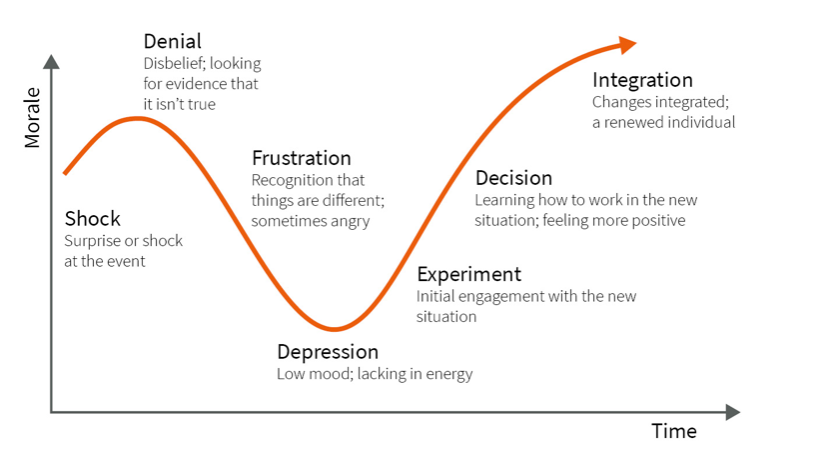
For example, we take electronic vehicles and battery cars (Electronic Vehicles or EVs). Some of us were front runners by already buying the first Tesla Model S back in 2013, while others didn’t have the financials to move to EVs, even though they still wanted to. Some of us are still true petrol heads, and like the sound of real engines and the gasoline smell. The difficulty in change management and changing behaviors lies in the speed of going through this curve or accepting a particular change. This is not the same for everyone. Also, the starting point is different for everyone. If we want people to switch from petrol cars to battery cars, the “awareness” campaign for petrol heads most probably will be different from the ones that don’t have the money for it.
Another insightful view to change is that of John Kotter, who describes the “Eight reasons why transformation fails.”[2]. These are the following reasons:
- Lacking a Sense of Urgency
- Lacking a Powerful Guiding Smart Coalition
- Lacking a Vision
- Under-communicating the Vision by a Factor Ten
- Not Removing Obstacles to the New Vision
- Not Systematically Planning for and Creating Short-Term Wins
- Declaring Victory too soon
- Not Anchoring Changes in the Corporation’s Culture
If we retake battery cars as an example, we see that EVs are currently the most sold cars in Western Europe, beating petrol cars. This means that we can consider the change to EVs successful. If we assess the EV developments over the years against four of the eight reasons why transformation fails, it becomes clear why the EV transformation is a successful one:
- Over the last few years, there has been an increasing sense of urgency that we can’t continue burning fossil fuels as we did before. We need to change if we want to survive as species. Like Al Gore already announced in 2007 in his movie “An Inconvenient Truth,” where he showed the world the urgency for climate change.
- The end of the petrol car is coming closer. Governments have pushed changing to EVs for several years now, where Elon Musk, as an extravagant entrepreneur, also had a positive influence. After Tesla’s impressive growth, most existing car manufacturers switch to making EVs. This reveals a robust and future guiding smart coalition.
- Elon Musk started Tesla with the vision to “Create the most compelling car company of the 21st century by driving the world’s transition to electric vehicles”. With the Lotus Elise EV (Tesla Roadster was based on this car), he proved that an EV car for daily life was possible. With the Model S, he showed that it could even be a compelling car, with an excellent iPad console that looked and drove like a sports car. With this, he also revealed that with Systematically Planning, he could create Short-Term wins, with first the Roadster and then the Model S. However, Tesla is currently doing practically no innovation anymore in their design and hardware and is nowadays missing a compelling vision compared to, e.g., brands like NIO or Rivian.
- The most critical obstacle for EVs was, and maybe still is, the price. Governments removed this obstacle by subsidizing the purchase of cars massively. At this moment, these subsidies are diminishing since the costs of EVs are lowering.
We don’t know if Elon Musk used Kotter’s “eight reasons why transformation fails” but his buyers definitely went through it perhaps without knowing it. Still, the above example does show that these reasons can give excellent guidance in any shift or change, including Information Security. Therefore, in the next section, we will provide some propositions on how to make a successful transformation in security behavior based on Kotter’s eight reasons.
Make people want to understand the change, to make the change
So, when you start your Security Awareness month or set out the actions to change behavior, consider Kotter’s approach to the change curve and the eight reasons why changes fail. Here are some propositions
- A sense of Urgency is mostly there since cyber-attacks are a global threat in everyone’s life, and if not, make it explicit or use an analogy.
- Get people on board from all levels in your organization and make them your security ambassador within your company. Leading by example by the leadership team is critical. Since many people copy the behaviors and manners of their leaders, this inherently means security leaders need to get sufficient airtime at the Executive Leadership and Supervisory Board to share and discuss what is expected. By doing this, a powerful and intelligent security coalition is formed.
- Create a compelling vision. For this, read our blog on Compelling vision, which elaborates on why emotional engagement is a must to change people’s attitudes from “I have to” to “I want to.”
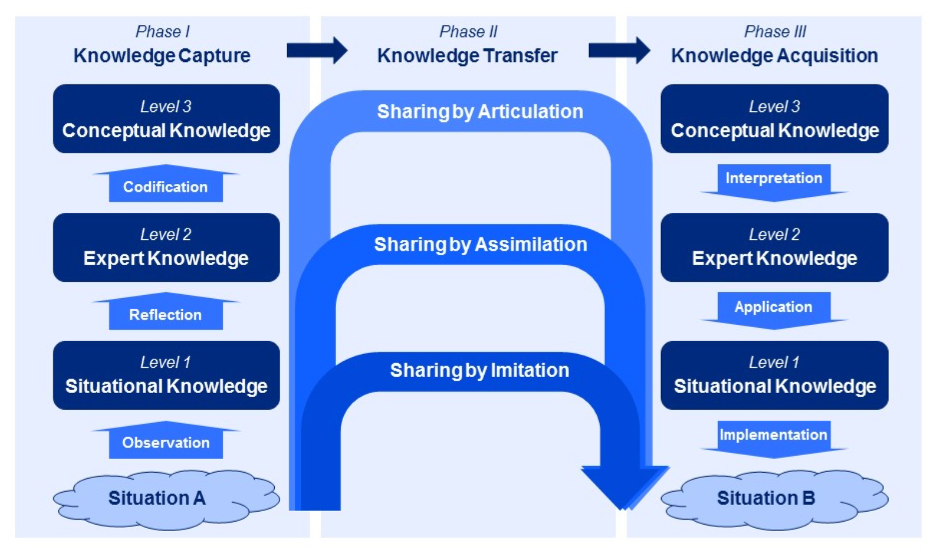
- Communicate as often as possible about security, so everybody understands the Why and the What, just before it gets annoying. Not only by email but in every conversation, town hall, presentation, or another form of communication you have in your company. In this blog we elaborate on this. Keep in mind: People accept more when they are approached nicely. In knowledge transfer, it is essential to understand the level at which you need to share your knowledge. The conceptual model “knowledge sharing bridges[3]” was developed by AMS professor Ron Meyer. On the left side is the sender, and on the right is the receiver. A security professional, the sender, often communicates on an “expert knowledge” level, while the receiver needs to start with “Conceptual Knowledge.” In the end, the receiver needs to put the knowledge into practice by “copying” or “imitation” the knowledge of the sender in its situations (situational knowledge). Often this last step is “learning by doing.”
- Make sure you remove obstacles like “I don’t have time,” “It’s user-unfriendly,” etc. Take user experience when selecting security technology and get buy-in from the management that can make people available.
- Show a plan for security behavior and show progress and “wins.” This means that behavior needs to be measured, and the outcomes communicated. The most common ones are the outcomes of phishing tests. Other measurements for behavior can be the number of screens not locked, the use of easy-to-guess passwords by cracking the password hashes, the number of reported security incidents, and phishing emails. Encourage people and celebrate a successful phish.
- Don’t think you are secure if you have the newest security awareness and phishing tools. You are never done, and new people will join the company that might not (yet) show the required secure behavior.
- Making sure that behaving securely will be like driving a car. Unconsciously doing it right is only possible after having a lot of flight hours. Important in this is to recognize that not everyone is in this phase yet. “The Learning Stages,” created by Noel Burch[4] explains the stages a person goes through in developing competencies. People can fall for a phish because they are unaware that phishing emails exist. After that, a person does know about phishing and learns about their incompetence directly after falling for a phishing mail. When a person analysis every incoming email for phishing, the person becomes conscious and competent. At the end, when people have seen enough phishing emails and keep up with the latest development, they will unconsciously do the right thing. People need to know where they are in these stages and their blind spots. Unconscious Incompetent might be the scariest one since, at that stage, they don’t understand what the fuzz is all about and think they know what to do.

Change the Organization by Changing the Individual
Although we fully support Security Awareness month and Security Awareness training in general, we think this is only a small part of achieving the primary goal of having people behave securely.
Changing the behavior of individuals to a more secure one must be approached as a change or transformation program. Methods like a fine or penalty for speeding and non-compliance give temporary impulses and will not have a lasting effect. The same goes for FUD (Fear, Uncertainty, and Doubt) which you can also read in one of our blogs. Therefore, we think that changing or transforming specific behavior can only be done more positively. This will change my mind from “I have to” to “I want to.” E.g., “I want to drive as fast as the speed limit because that keeps more people safe” instead of “I have to keep myself to the speed limit because of all these illogical rules that lead to a fine if I don’t comply.”
Management models like that of Kotter can help you define and execute the appropriate activities to make that change in specific behavior. Using such a model is not a one-time exercise. A compelling vision that worked before might no longer work in the future, as a problem Tesla now might have with outdated designs and compelling competition from Asian markets.
Now, let’s make October Security Awareness Month a success, and let’s think about the rest starting from November!
[1] The Kübler Ross model is described in the book On Death And Dying by Elisabeth Kübler-Ross
[2] Leading Change: Why Transformation Efforts Fail, John P. Kotter, Harvard Business Review, 1994
[3] https://c4sl.eu/portfolio/23-knowledge-sharing-bridges/
[4] https://www.gordontraining.com/leadership/four-stages-learning-theyre-circle-not-straight-line/
[5] https://medium.com/outco/3-models-for-better-learning-6f638a066e2e
