Introduction
Security departments are growing out of their seams. While demand for cyber security professionals is growing, finding and retaining good staff takes hard work. According to the 2022 (ISC)2, Cybersecurity Workforce Study 1, about 70% of respondents said their organizations don’t have enough cybersecurity employees. And while the number of professionals is growing, security is not at its required levels yet. Are we utilizing our resources wisely? If so, you can ask, why, then are companies still being hacked? Maybe we are doing something wrong here because cyber threats and regulatory requirements are increasing in this digital era. This article will endeavor to address several generic pitfalls and industry-specific flaws that require attention.
Current situation
The current approach in cyber security needs to be corrected in the basics. Some take the word cyber security literally and “try” to protect “cyber,” which is undoable since cyber as a concept is endless. This makes cybersecurity a “wicked problem.” In 1973 design theorists Horst Rittel and Melvin Webber suggested that wicked problems have specific characteristics:
- They do not have a definitive formulation.
- They do not have a “stopping rule.” In other words, these problems lack an inherent logic that signals when they are solved.
- Solutions to wicked problems are not true or false or right or wrong, but rather better or worse.
- There is no end to the number of solutions or approaches to a wicked problem.
- Wicked problems can always be described as the symptom of other problems.
Rittel and Webber…”Climate change, like problems in an education policy or public health, is a wicked problem. It avoids straightforward articulation and is impossible to solve in a way that is simple or final.”[1] We, as researchers and practitioners, observe a natural tendency to throw more resources at the cyber security problem, hoping this might solve it. But we tend to forget that simply throwing money at; buying more tools and services capable of managing cyber security is not the solution. It might be a way to get to the required security maturity however, it is not the most efficient and not the most effective or sustainable one either. This is the main reason why we refer to “Digital Security”.
A Security Manager once told me some twenty years ago that his main goal was to make himself obsolete. When that happened, he knew that information security – now branded as cyber security – was embedded across his organization. While some security professionals might think this is a utopia, setting this as the main goal is the key to success.
Let us elaborate on why we think having less, or no, cyber security staff should be the ultimate goal to make cyber security a formal management discipline.
People will only take ownership when they feel accountable.
“People Support What They Help Create.”
This principle is one of the greatest lessons that any leader can learn because if we want the commitment of our people at the point of implementation then we need to involve them at the point of creation.
In many organizations, cyber security professionals often take over parts of the work of the people being accountable for the implementation and maintenance. In practice, people will sit back and look at the security staff to do it for them. For example; patch management is a crucial and repetitive task vital for any organization. We often notice that a security professional does vulnerability monitoring. Once a vulnerability is identified, a ticket is registered in the ticketing system, alert emails are sent, and people are called to mobilize IT staff to apply the necessary patch. In applying the patch, progress is monitored, and systems are scanned to verify whether the patches are applied by the security professional.
While this all might get the job done, it’s the world upside down. It’s not only inefficient, but it’s also annoying for IT staff being chased and security professionals that need to pursue IT staff. You don’t ask your neighbor to empty your dishwasher and chase him if he forgets. It’s your role and your accountability.
The main issue we observe is that when security professionals are filling the gap IT staff is leaving, is that it will become a never-ending story that is too dependent on individuals and not sustainable. We refer to the “compensating trap” behavior. The problem is that although IT staff might be accountable in the organizational chart for vulnerability and patch management, they sometimes don’t feel that responsibility for it if they don’t take ownership of this process.
The reason why people might feel they aren’t accountable and don’t take ownership can be diverse. Some of the reasons might be a lack of education or a need for more awareness about their roles and responsibilities. Another cause might be that it needs to be a Key Performance Indicator (KPI) on which the management of the IT department manages them. Or even a KPI for the IT department itself. In the book “Critical Success Factors for effective Business Information Security,”[2] one of the Critical Success Factors is clear roles and responsibilities with KPIs. To change this, not only does the governance of IT need to be changed, but also the mindset and behavior of IT staff need a change through training and education. Changing people’s behavior is, however, not a one-time activity and could depending on the size and complexity of the organization take month to even years. That’s why this needs to be approached as a change program.
A positive result of IT staff taking ownership is that things can be more effective and efficient. IT staff likes automating things, so they will do the same with security management, making it more efficient and effective. Our experience across multiple companies shows that this leads to a reduction in “waste” of time and money. Sustainability is the most significant long-term benefit of improved ownership, craftsmanship, and automation.
Delegate, Delegate, Delegate
By now, you might think, “but security is such a broad profession, I don’t think that I can reassign all the work to different departments.”
Of course, that is partly true, and you probably can’t reassign all work. The “mastermind” in security, the leader of security needs to remain in charge of leading security in the right direction. Let us take a closer look at all the tasks and see what can and can’t be reassigned, with the assumption that we can change and educate the people in IT and Business processes to be able to take the necessary ownership.
An overview of all security tasks is created and updated by Rafeeq Rehman in his CISO mindmap[3]. Our aim is not to present a complete list here, but mainly to provide general guidance on the most common responsibilities. The 2022-23 version is the latest, but the 2021 version seems visually easier to read.
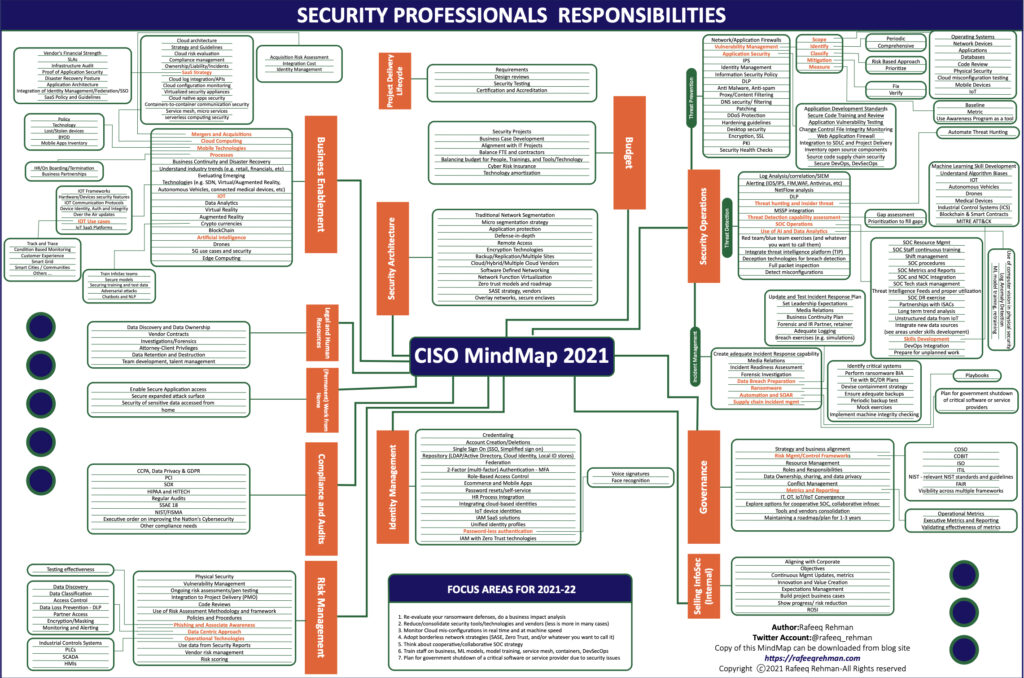
Figure 1 The Chief Information Security Officer Mindmap 2021, by Rafeeq Rehman
Based upon the CISO MindMap, we conducted an assessment per area to which level cyber security activities can be assigned to -other- operational processes (IT and Business):
- Business Enablement. This area focuses on security in technologies, sourcing models, M&A, and safety within business processes. Security professionals want to be involved in all these areas, set the relevant security guidelines, design the strategies, and monitor compliance with these requirements and procedures. In practice the downside is that security professionals are not involved, don’t have the proper knowledge for all these areas, or don’t have the time or expertise to support the business. This impacts the effectiveness of security maturity. A different approach is not focusing on bringing the proper security knowledge to the table but ensuring that the people responsible for these business areas understand security risks, know the latest security practices and technology, and ask for help where needed. This means that CISO can support education, expertise, or exercises. The advice here is not to use jargon and abbreviations and train yourself in business “language.”
- Project Delivery Lifecycle: this is the process for new developments from requirements to testing to certification. With the proper implementation of Security by Design or Secure Application Development, this process is suitable for assigning all activities to those responsible for delivering developments or projects. Education, training, but also tooling can support this process sufficiently.
- Security Architecture: Today enterprise, domain, solution, and product architects have security as part of their education and experience, incorporating it in their designs. Likewise, suppliers push security configuration as part of their solution. Since most of these architects are also domain or solution experts, they usually understand what to implement and how it can be implemented successfully. Where things can’t be implemented, a security or risk expert might come into play to determine whether certain risks should be taken. However, in the end, it’s a business decision, so one should question whether a security expert must come into play.
- Legal & Human Resources: On the legal side, our experience is that if you have the correct legal and privacy expert, the added value of a security expert is to support in translating specific legal requirements into tangible measures or translating these measures into the level of compliance to particular rules. However, whether specific incidents or lack of measures have a legal implication is something a legal expert understands much better. Where a security expert might raise a red flag for GDPR compliance, a legal expert might see this differently based on experience and jurisprudence. The human resource part regarding the development of people is part of the manager’s role. However, for new products in security, security experts must be involved in guiding the development of people in the right direction for the future. Another important aspect is to develop clear KPIs for managers about specific security objectives. Where they can take ownership over these objectives and KPIs might evolve since the maturity process requires different approaches and changes. That can be incorporated into the HR role descriptions. Our experience is that those clear role descriptions based on European Competence Framework (ECF) and transparent assessment criteria will receive lots of enthusiasm.
- Work from Home: Working from home has been a specific area of attention for security experts, but COVID-19 made a secure way of working from home something fully designed and implemented by architects in collaboration with infrastructure and workplace staff.
- Compliance and Audits: Security controls from the relevant compliance frameworks must be designed, implemented, and tested. Operational activities should deal with implementing these controls and delivering the evidence pertinent to test the effectiveness. This seems like an open door, but we still observe many ISO’s doing this testing work instead of the responsible line manager. The same as in our example of patching; this is compensating behavior. Proper governance is needed to implement this behavior and mindset—governance in directing, monitoring, controlling, and communicating. Security is a functional leadership capability rarely hierarchical. This functional discipline is necessary within the strategy, and auditors must form a judgment over this. We believe that bringing this -functional- leadership and governance into place helps significantly to anchor cybersecurity for the long term and pass audits successfully.
- Risk Management: The subject in the Mindmap is broader than just pure Risk Management. Rehman emphasized all activities you can undertake to identify, assess and mitigate risks. You want all your first-line managers and product owners to be equipped with this capability. Provide them with clear instructions, guidelines, and training so that they can do the following:
- Identify new risks that need to be identified via pen-testing or red-teaming activities. The business is active in all environments, such as Industrial Control Systems, Point of Sales systems, or Cloud.
- Tooling can support this. Many vendors provide essential risk and vulnerability functions, so product owners, engineers, and developers can do this to support daily operations.
- Physical security is often specific expertise too broad for Digital Security experts to understand, identify, and asses what your facilities department understands better and what effective treatment plans look like. Since many of our physical devices are connected to the internet, it is good to collaborate with first-line facilities and safety departments.
- Vendor Risk Management nowadays is an integral part of Vendor Management and the procurement process; they might need some education and training where digital risk metering technology can support the security department in identifying rogue or orphan assets. It can also help the procurement officer identify the supplier’s risk posture. Or to identify third-party risks in the supply chain. This becomes more eminent in NIS2, the DORA act, and other legislation[4].
- Policies are usually standard and widely available for copying. However, this might need some guidance from a security expert about what is feasible for the organization. Our best practice described in previous papers is applying the Kipling method to corporate policy, a technical standard or procedure, so it provides the precision needed nowadays. The Kipling method[5] is also known as the 5W+1H method by Rudyard Kipling. Kipling is common practice in auditing[6] Mills stated, “The auditor should always use Kipling’s checklist… during this stage of the auditing process. In Zero Trust, conditions for access are formulated in an abstract (i.e., technology-independent manner) via the Kipling method: WHO gets access, WHAT exactly access is provided, WHEN, (from) WHERE, WHY, and HOW (i.e., under which conditions is access granted). This allows first-line managers or product owners to implement the vendor-neutral policy and prevents the security staff from doing it via “compensating behavior.”
- Awareness can be fully incorporated into the Human resources and Learning & Development departments. Our experience is that L&D staff understands how people learn and how knowledge is transferred sustainably. Using intelligence learning experience platforms, learning experience methods, and interactive games, they know how to design and create the most effective training. And this can, most of the time, create more effective and fun activity than we have ever seen security staff doing.
- Identity Management: Security experts can set the requirements, e.g., MFA (Multi-Factor Authentication), and a “need-to-know” basis. They know how to design, adjust, and make processes as SMART as possible. However, our experience is that when Businesses and HR understand access control and identity management, it is much more effective and efficient that they will implement and maintain this themselves.
- Budget: Make all security expenses part of the regular IT and Business Operations Budget. Security departments often don’t have a budget and need others to purchase. When you make security part of the budget of everyday processes, they will do something with the money spent to make it a sensible investment. E.g., Why should investing in EDR (Endpoint Detection and Response) software be a responsibility of IT while buying Anti-Virus scanners isn’t?
- Security Operations: A lot of digital security operational work needs to be performed by IT. In the previous section about vulnerability management, you read more about our view on this. Security Monitoring, however, is a specific activity and crisis management. However, when reviewing current security monitoring software and the SOC’s (Security Operations Center) work, we noted that more and more knowledge for analyzing is part of the tooling. A well-educated IT administrator and network engineer understand certain events well. The main question is, however, the 7*24 monitoring that you might need when IT needs to do that or is capable of doing that?
- Governance & Selling Digital Security (internal): this is the primary role of the digital security leader. Governance involves leading and managing security within the company over the whole company and not micro-managing it. Selling Digital security is an integral part of governance to set goals, lead people to achieve these goals, monitor progress and adjust where needed. To do this, stakeholder management (including selling) plays a significant role.
The above shows that a lot of the tasks of a security professional (or CISO) can be executed by people in the IT and Business processes. Instead of hiring more staff, reduce staff acquisition and delegate it to existing methods.
By doing this, we establish a formal risk and security function “engineered” into the organization (a.k.a. the discipline of enterprise engineering[7]) with proper governance and management and utilized by transparent, structured processes and relational mechanisms that embrace automation and speed.
Focus on what’s essential and reuse what you can
When a company becomes regulated, e.g., financials, pharma, Stock exchange listed, assurance statements, and security certifications come into play. This increases the amount of overhead in digital security. Mainly due to the different reporting processes regulatory bodies require.
These developments and requirements significantly impact the efficiency and focus of a company and the security department. A common condition is performing periodic documented and auditable risk assessments. Although assessing and analyzing risks is essential, the work associated with current risk assessments is immense. Often the requirements for risk assessments are created by people who studied risk methodologies and have the time to develop complex risk models and extensive risk questionnaires. While managing risks might be a daily discussion, organizations must document these assessments to make this as easy as possible, e.g., with some small and proportional-oriented questionnaires. In the end, our experience is that most security requirements are by default necessary, and only for some, it needs to be decided whether it is required. The main reason is that about 10-15 years ago, specific security measures like encryption and redundancy were expensive and difficult to implement. Nowadays, you can get encryption for free on a hard disk level, and redundancy can be achieved in the cloud with almost a button click. So many old-school and traditional controls come either out of the box or must be more relevant in certain situations. So, applying a proportional amount of controls to treat the risk cures the patient; too much treatment with medicine can kill the patient. In other words, it suffocates business operations.
A significant amount of documentation and an audit trail is needed for compliance, which can be time-consuming. In our experience, a central Information Security Management System (ISMS, not the ISO27001), an application, automating and centrally documenting all required privacy, risk management, and security control evidence, is very efficient. As we had two decades ago, before MCI and Enron scandals, we documented financial processes in separate excel based systems proven not to be sustainable. This urges the need for ERP (Enterprise Resource Planning) and economic systems like SAP or AFAS. Mainly because financial processes require a single version of the truth, which is happing now in the security space as well. Tighter regulatory requirements urge a professional level of Administrative Organization and Internal Control. Specific Governance, Risk, and Compliance (GRC) tools embody ISMS functions but are, for many organizations, an overkill. Managing a GRC becomes a task on its own. This can suffocate the business mainly because these tools are complex. Basic Information Security Management Systems facilitate automated control testing and can create periodic tasks that need to be executed by operational staff, which they might already be doing. Centrally documenting the outcomes of controls will make Governance over Digital Security and complying with frameworks and requirements a “Test once Comply Many” way of working. We do what we must to govern our security maturity and reuse it to comply with external frameworks.
Stop the compensation trap.
A "compensation trap" refers to a situation where an individual or organization becomes reliant on compensating or a temporary fix for a problem rather than addressing and solving the root cause of the problem.
By removing the security safety nets and embedding security tasks inside the organization the “compensation trap,” as explained in the aforementioned, can be removed and eliminated over time. More often than not, when a security professional asks an IT employee why specific changes were not done yet, the answer might be that an essential ERP or Digitalization project was more important or that they thought that it was “you from security that was going to do that.” When this safety net of compensation trap behavior is no longer around, they must start arranging and planning themselves. Think about the adolescent constantly lying on the couch gaming when living with their parents and unwilling to make a healthy meal. When that adolescent finally lives by themself or becomes a parent, most of them will be capable of making a healthy meal, decent living, and even raising an infant. This is what refers to as the process of maturing[8].
Conclusion: Future digital leaders lead and think as C-level
The growing number of security personnel needed in companies is not a sustainable way forward. This is not caused by the scarcity of good security staff in general but by our belief that security can only be effective and efficient when people accountable for the execution of security measures take ownership. These first-line business people operationalize the tasks daily, have all the insights into how they work, and usually know how to organize their work efficiently. Simply throwing more people at this Wicked Problem that continues compensating the wrong behavior will not contribute to security maturity enterprise-wide.
This change in behavior does not remove the need for security experts capable of leading digital security at a sustainable level. They should be capable of overseeing where measures are implemented successfully and where additional attention is needed, with the capability and courage to change the status quo and people’s behavior, and institutionalize it as a function without the enterprise-wide “compensating trap” behavior.
Galina Antova in her article “Why CISOs Make Great Board Members”[9] suggests that the role of the CISO has evolved from being a risk metrics presenter to a translator of risk to the business. Therefore, the expertise CISOs have developed in recent years in explaining risk to the board makes them valuable contributors to these conversations.
Consider what your company’s CEO, CFO, or CIO is doing. They lead the company and manage others to achieve specific goals instead of micromanaging operational staff. So, to learn from them, one can start thinking as a C-level player, set clear goals, roles, and responsibilities, capture these goals and KPIs into your central ISMS, functionally lead people to encourage first-line ownership and monitor and report on the effective execution. Less is More.
[1] Rittel, H. W.,; Webber, M. M., cited work, Dilemmas in a General Theory of Planning., Policy sciences, 1973, page 155-169
[2] Y. Bobbert and T. Papelard, Critical Success Factors for Business Information Security, Antwerp: Diagloog Publishers, 2018.
[3] https://rafeeqrehman.com/wp-content/uploads/2022/04/CISO_Mindmap_2022_no_headings.pdf
[4] The NIS Directive is the first piece of EU-wide legislation on cybersecurity. The Directive on security of network and information systems (the NIS Directive) Requiring member states to be appropriately equipped. See: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52020PC0823&qid=1681116036420
The DORA is designed to consolidate and upgrade ICT risk management requirements throughout the financial services sector to ensure that all participants of the financial system are subject to a common set of standards to mitigate ICT risks for their operations. European Commission, And the Digital operational resilience act (DORA) for the financial sector and amending. Source: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52020PC0595
[5] Kipling, R. “Just so stories”, Double Day, 1902
[6] Mills, D., Working Methods, Quality Auditing, 1993, page 122-142
[7] Enterprise engineering is the body of knowledge, principles, and practices used to design all or part of an enterprise. An enterprise is a complex socio-technical system comprising people, information, and technology that interact with each other and their environment to support a common mission. Source: https://en.wikipedia.org/wiki/Enterprise_engineering#cite_note-Gia10-1.
[8] In the book on Maturing Business Information Security all these processes are dealt with phase by phase and what is needed after level 3 or 4. In terms of administration, internal control and (high levels of) automation. Source: https://repository.ubn.ru.nl/bitstream/handle/2066/192437/192437.pdf
[9] https://www.securityweek.com/why-cisos-make-great-board-members/
