Every day we get overwhelmed with information about cyber security. Whether it is security staff monitoring security logs, IT staff constantly patching, or managers hearing about required improvements, the list goes on and on. As a result, people develop cyber security fatigue. Cyber security fatigue can also be defined as virtually giving up on proactively defending against malicious actors. According to a CISO benchmark study of technology vendor Cisco, 42% of the surveyed respondents suffered from cybersecurity fatigue[1].
As we mentioned in our previous blog, “Why Fear, Uncertainty, and Doubt (FUD) fails in Digital Security and being BAD prevails,” information about threats and cyber risks will get our attention in the short term, as bad news does. Still, it will not keep our attention in the long term. Think about certain high-impact news items that first are part of our daily life, will soon get less of our attention, and, in the end, not seem to bother us anymore. Cyber security fatigue is a problem for security staff and IT staff, Management, and even end-users. The following section will address this fatigue for the different stakeholders in information security and provide steps to prevent this.
The Risk of Combat Exhaustion for Operational Security Staff
A comparison can be made to investigate that impact on security staff, e.g., operators in Security Operations Centers (SOC) or Incident response teams (CSIRT) with the soldiers in combat. Both are fighting an enemy, one virtual, the other physical.
There is a lot written about combat stress and its impact on combat efficiency when researching army literature. In the book “On Killing” by army veteran Dave Grossman, the relation of stress and the development of combat exhaustion to the combat efficiency of the average soldier is described and visualized in the curve below.
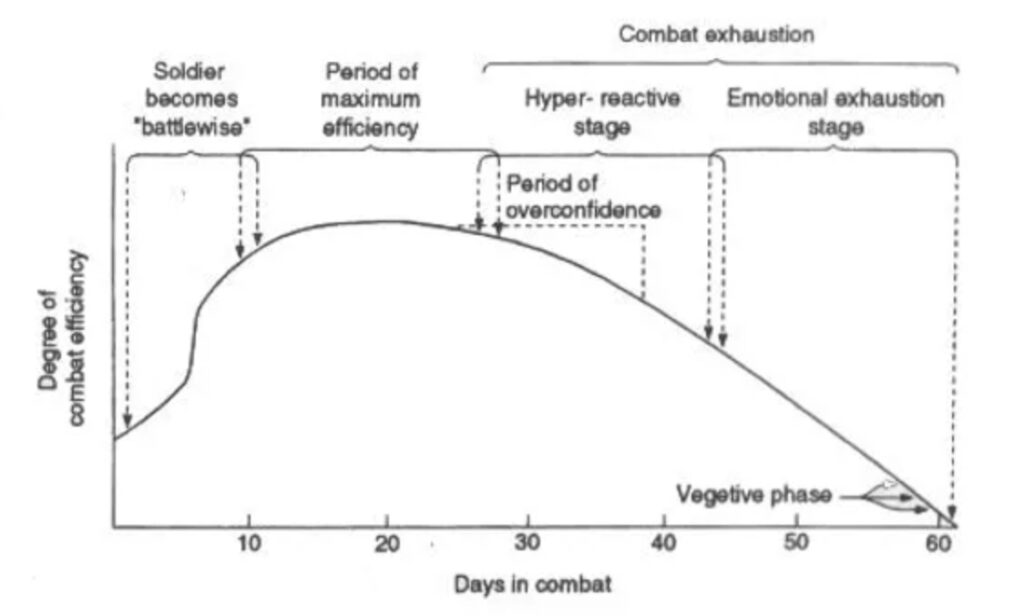
After about ten days in combat, the soldier reaches maximum efficiency; however, the efficiency decreases after thirty days of fighting. Of course, it is crucial to understand what combat stress is. In the Leaders’ Manual for Combat Stress Control of the Department of the Army, a distinction is made in several stressors. These stressors are included in the picture below.

Although several stressors applicable for soldiers in a physical battle are not relevant for cyber warfare. In cyberwarfare, the cyber soldier has no risk (yet) of dying in combat, and the environmental stressors are less pertinent. However, several of the Physiological, Cognitive, and Emotional are applicable. To control this combat stress for security staff, the following can help to prevent the stress and keep cybersecurity staff effective and alert for combat:
- Automate the analysis, interpretation, treatment, and handling of log events. This way, only accurate information requires action;
- Make sure that workloads are divided across different teams or staff. This way, all staff gets the same experience in combat but also create leeway where there is less time pressure
- Have clear standard operating procedures (SOP’s) and train them. This way, it is clear who needs to do what and when. SOP’s are common in aviation, military, and lab environments where checks and balances are necessary to avoid catastrophes or atone phase three and four in the curve (combat exhaustion).
- Keep the “fun” at work. Don’t tell people constantly about the fear of hacking, but keep it also light in some cases. Showing a YouTube movie from the Russian Federal Security Service (FSB) catching the REvil ransomware gang in their underwear portrayed as filthy nerds might also put things a bit in fun and perspective.
- Stay connected with your people emotionally and don’t just see them as computer machines dealing with nerdy stuff
The risk of Indifference from your IT staff
Essential people in implementing and maintaining the security measures in an organization are the people from IT. To keep the environment secure, they need to patch and update systems timely and often ad-hoc; they need to ensure that security systems run and follow strict procedures. Built and develop secure code, safeguard backups, test restore processes and be careful with opening new connections to the outside world—all to keep a security incident from happening. And when something happens, they need to work during nights and the weekends to get everything cleaned and restored in time.
When nothing happens, the need to perform these “Standard Operating Procedures” might become less relevant for IT staff since they spend a lot of time on these ‘household” activities but never experience the added value when danger arises.
To make sure that IT staff keeps following the Standard Operating Procedures, it remains crucial to:
- Update IT staff what the value of their activities is. This can be done by, for example, demonstrating to them how hackers work and what techniques they use in combat.
- Support IT staff in automating their tasks to limit the time on mind-numbing tasks and involve them in more energizing work.
- Involve and “engage” them in decisions about new or changing security measures. Rotating jobs also help to keep first-line professionals activated and alert.
The risk of underestimating by Management
Another stakeholder in information security that might suffer from Cyber Security Fatigue is the management of an organization. Security professionals constantly talk about security threats and need a budget, which never seems enough. Next to that, external stakeholders, customers, and regulators require more and more certifications and control statements to prove that a company’s security is guaranteed. While starting a security improvement often begins as a very well-supported program, in time the “never-ending story” loses interest since progress is slow or the added value remains unclear.
To prevent Management from losing interest in getting Cyber security fatigue, the following can be considered:
- The principal starting point is to assess your own Cyberleader (sometimes referred to as the Chief Information Security Officer) and their capabilities in developing a vision and a plan that suits the organization’s needs.
- Make investments in cyber security in dialogue with management and based on “real” risks rather than theoretical ones. Management nowadays is fully aware to which level they want to accept risks. Be aware that not all organizations and management are similar. So, applying a “one size fits all” approach might not work. In a company where the founders are on the Board, the acceptable risk level might be higher than in a company with a hired Board or when the company is under regulatory supervision. In general, entrepreneurs take a higher risk than managers that are part of a Board, and personal agendas play a role. We intensively describe these silent enemies in our book.
- Measure and report the effectiveness of your security investments, or communicate the Return on Security Investment (ROSI, we explain ROSI in this previous blog: Digital Risk to the Business, what do they cost), just like any other business process or investment.
- Strip all the facts from Fear Uncertainty Doubt and other fuzzy jargon, challenge and scrutinize the real priorities. Maintain a military discipline in overseeing any violation of Standard Operation Procedures.
The risk of recklessness from end-users
A study from the National Institute of Standards and Technology (NIST)[2] found that most of the typical computer users they interviewed experienced security fatigue that made users show risky computing behavior at work and in their personal lives. This is caused by the security measures the users face in their day-to-day work and life. A well-known one is the massive number of passwords a user needs to remember to access their data.
To respond to cyber fatigue, the NIST researchers offer three specific suggestions:
- Limit the number of security decisions users need to make;
- Make it simple for users to choose the right security action; and
- Design for consistent decision-making whenever possible.
This means that in the design of a system, the ease of use of security measures needs to be considered. Also, training of users in the use of security measures and monitoring of “risky” behavior should be considered.
Conclusion
Distinguishing facts from fiction is a significant challenge in our industry. Cyber risks have become part of our daily life and business. The constant pressure of threats, mandatory procedures and mind-numbing manual tasks wears people out. This gives us a severe risk to the effectiveness of security measures and the security level in general. This is why we advise companies to learn from military procedures and adopt our four steps to cope with Cybersecurity fatigue. Digital leaders should be aware of cyber security fatigue and take the relevant precautions to prevent this from happening.
[1] Securing what’s now and what’s next – 20 Cybersecurity consideration for 2020 – Cisco Cybersecurity Report Series 2020, CISO Benchmark study
[2] Security Fatigue, in IT Professional, Sept.-Oct. 2016, pp. 26-32, vol. 18
