Much uncertainty and fear are sown in the media about Ransomware attacks. Whether Ransomware is a big problem remains to be seen. Recent research shows that ransomware has no impact on the economic value of the organization1. The question is more what form of impact we know; technological, political, economic, or social. We know from experience that the stock price is not the only yardstick for determining the effects of Ransomware, but also the perceived value, such as the degree of reliability (Trust). The fact that Ransomware has an impact seems undisputed; the fact that there should be more focus on prevention than on cure also seems undisputed. But how do I do that as an executive board member or supervisory board member, and what questions can I ask.
In the context of “prevention is better than the cure,” we summarize several core interventions that prevent Ransomware attacks and the right question that you as a board can ask your security professional.
We focus on Ransomware and other types of attacks with known techniques, such as advanced hacks to steal or spy and DDOS attacks. To limit the “blast” as well as the “blast radius”. Therefore, we speak of ‘left of bang’ measures in military terms.2

The term Left of Bang refers to the attack timeline where Bang (in the middle) is the attack. Everything to its left precedes the attack, and what’s on the right follows. Left of/before the attack is the time for proactive prevention. Right of/after the attack begins is when reactive countermeasures take place. Left of Bang is obviously where we’d want to stay, and to do so, we’d like to detect early warning signs, which we can then disrupt or avoid to prevent the attack.
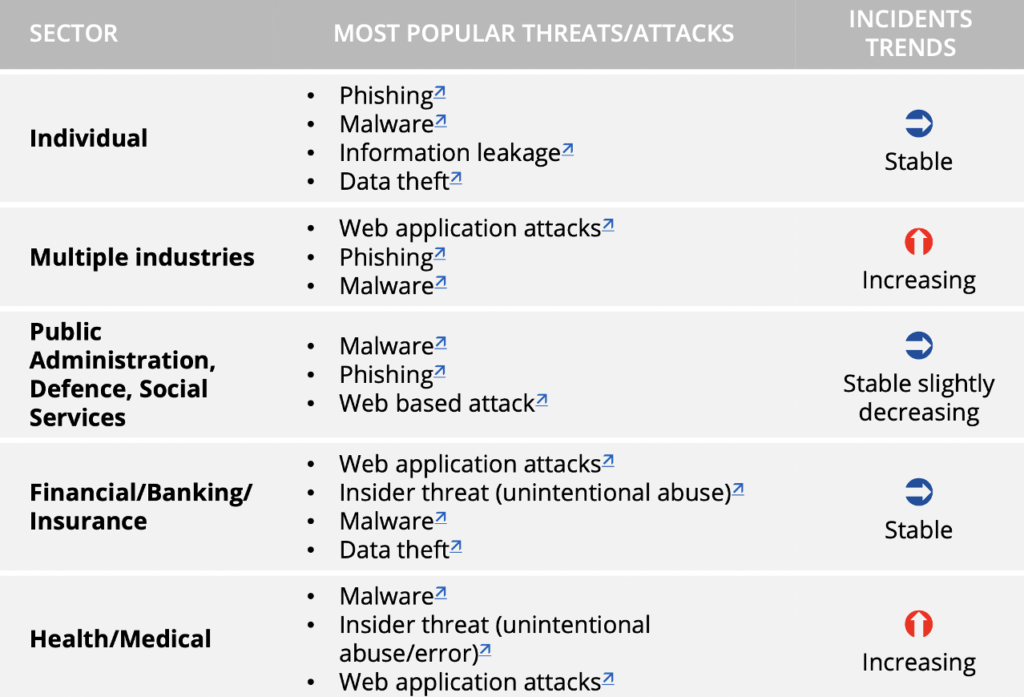
We base our advisories below on analyzing the known hacker groups listed on this MITRE site (MITRE, 2021) and their attack techniques.
Left of Bang
1. Endpoint prevention and Securing the perimeter
Most attacks start with penetrating an “endpoint” (usually an employee workplace) or phishing of user password credentials. From that point on, an attempt is made to approach the rest of the network, move laterally, and collect information. Think of phishing emails, which sometimes seem very realistic, for example, a “Curriculum Vitae” attachment in an email to Human Resources for a job application, which contains malicious code and thus gains an access point to the network. Or a phishing mail is guiding you to a website that looks very similar to a genuine Microsoft Office365 login but is fake.
Therefore, it is vital that this code cannot be executed to repel the attack, and credentials can’t be misused. In the meantime, several technology manufacturers have solutions for protecting these endpoints, focusing on the techniques used instead of known “signatures.” Technology like Threat monitoring, criminal group profiling via threat intelligence, behavioral analysis, etc., all residing “left of bang.” In the context of the fox that guards the henhouse, we advise you to take an A-brand technology manufacturer that has elevated Cybersecurity as its core task. A surgeon operating with a fork leads to misery. Another crucial preventive measure on the endpoint is ensuring that the endpoint is “hardened,” meaning that a lot of functionality that a hacker can misuse is disabled. This is important because hackers are also capable of circumventing the software of these A-brand technology providers.
Making stolen or “phished” passwords useless is simply done using Multi-Factor Authentication (MFA). The best approach here is to make sure that everything accessible from the internet is behind MFA.
The main question here for boards is: How do we prevent hackers from getting access to our environment?
2. Segment clients and servers
The moment an endpoint fails to repel the “attack,” the attackers will try to spread through the network to create the most significant possible impact and gather as much information as possible. Network segmentation and setting barriers can help. A first and simple step is to ensure that the clients are separated from the servers so that only traffic is explicitly allowed that is necessary for the application in question. Separating the clients from the servers is often a relatively simple step with quick results, given that an attack usually starts with the clients. An existing security solution (e.g., a firewall) can often be used for this. This is also a simple question that a supervisory director or director can ask his security people to remain “left of bang.” And should an endpoint be compromised, these tools also offer you analysis options to determine the “patient zero” to do a quick root cause analysis.
The main question for the board: How do we prevent a hacker from moving around in our network?
3. A clear access methodology
Ensure that all access to servers is configured as precisely as possible. The Kipling method – Who, What, Where, Why, When, and How – (5W1H) can help enormously. After all, the “malicious” code must find a way to communicate with the server in question. The stricter this policy is set up (so not just on paper), the greater the chance that this code will fail to become active.
The board’s question: Did we limit access on a need-to-know basis, and do we validate and monitor all the access activities on our High Valuable Assets?
4. Limited GOD rights
The number one target for hackers is the systems or access rights of the “IT guys.” IT Administrators regularly have full access, the so-called GOD rights to the entire environment from their workplaces, thereby eliminating the above security measures. Therefore, their “increased” rights to these systems are a popular target of attackers. Hence, this is also a simple control question that a supervisory director or director can ask his security people.
By applying the proper segmentation with the right policy and validating its implementation, including the administrator workplaces, this risk is drastically reduced, and an administrator can still do his job.
The primary question here: How do we deal with increased privileges on IT systems?
Don’t allow Trust
The above points are mainly aimed at the endpoints because they are often the starting point of an attack. The measures offered can be seen as the start of a Zero Trust security strategy.
Unfortunately, it is not only the clients where an attack can launch or spread itself, and it is good to repeat the above points in the server environment. By focusing on the most critical applications and processes (crown jewels) and tackling them at a time, the entire process remains manageable. It is essential to realize that every application or process included is a significant security improvement. Zero Trust speaks of Protect Surfaces, which protects such an application or process. Periodic validations, such as a Periodic Vehicle Inspection for the car, ensure that changes do not open doors in the network.
Environments set up following Zero Trust are significantly less likely and seriously less damaged due to a Ransomware attack. Because you simply limit the blast as well as the blast radius.
Right of Bang
5. Ensure continuity
In the above measures, the emphasis is on preventing, left of bang, a ransomware attack. However, should things go wrong and you end up in the “right of bang,” a backup is indispensable to prevent the attackers from winning. How often do we make a backup and sometimes do a restore test? It is a simple question that a supervisory director or director can ask his security people. After all, prevention is better than cure.
Several additional attention points and questions to prepare for a Bang;
- Ideally, there is an “offline” or “tamper-proof” backup so that the attack has no impact on the backup.
- If the backup is “online,” it is essential to approach it the same way as other “segments,” with limited access and a strict technical policy. Better to keep an additional “last resort” backup somewhere safe.
- Test the backup regularly so that it is confident that what can also be restored if necessary and there is an indication of how much time this will take. The more often you train, the better prepared you are for the “competition.”
- Have an Incident Response Plan that covers essential communication to all stakeholders and deciding when or whether to have the recovery started.
- Practice playbooks that guide you in a straightforward way through the incident and have everybody understand these playbooks.
- Have a recovery plan in place, with prioritization and lead times. Depending on the impact of an attack, recovery can take a long time.
- If recovery is necessary, first make sure that it is clear how the attack originated so that the same attack does not (immediately) happen again.
The primary question here for the board: What do we do when we experience ransomware?
Conclusion
Bruce Schneier once said; “the medic who looks over your bleeding body, saying: “That looks like a sucking chest wound. i’d get that checked if I were you”” to make the analogy with companies focusing on buying intrusion detection systems, but that doesn’t do the remediation and fix. Many vendors are fuzzy about what they do left or right of bang and do something to fix stuff. The media’s focus on the aftermath of Ransomware’s impact is good. But, still, the emphasis should also be on preventative measures. Like with COVID, the core focus should be on prevention, mouth masks, social distancing, and PCR tests, or the fire brigade that visits theaters, concert halls, restaurants, etc to validate whether the proper precautions have been taken to prevent and suppress a fire and emergency exits are available.
Testing your organization on Ransomware Readiness is vital nowadays and relatively easy to do. To remain left of bang, everyone plays a role in focusing more proactively on prevention, both the security professional and the board, by being more critical of their own IT staff and that investments should be balanced to assure business continuity.
1. Bischoff, P. (2021, September). How ransomware affects stock market share prices. Retrieved from https://www.comparitech.com/blog/information-security/ransomware-share-price-analysis/
2. The book: Left of Bang: How the Marine Corps’ Combat Hunter Program ….
Bibliography
ENISA. (2021, Nov ). ENISA Threat Landscape is emerging trends 2020.
Van Horne, P. (2014). Left of Bang: How the Marine Corps’ Combat Hunter Program Can Save Your Life. Black Irish Entertainment LLC.
MITRE. (2021). Attack Groups. Retrieved from https://attack.mitre.org/groups/
