There is a saying by Sun Tzu in the Art of War in which he states, “If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained, you will also suffer a defeat. ‘If you know neither the enemy nor yourself, you will succumb in every battle”.
Also, in the book About Face by Colonel David H. Hackworth, you can learn that “you take fewer casualties attacking than retreating: Your job is not to die for your country but to make the other son of a bitch die for his country.”[1]
How to know your enemy?
As mentioned by Sun Tzu, it is crucial to know yourself and to know your enemy. In general, we can distinguish the following “enemies” in digital security[2]:
- (Organized) Crime: Profits mostly drive these cybercriminals. They are typically looking for personal sensitive information or to hijack and ransom your digital system’s resources.
- State-Sponsored: Groups with political, economic, technical, or military motivation. Often interested in competitive information or information about users for espionage purposes.
- Hacktivists: Their goal is to either create high-profile attacks that help them distribute propaganda or to cause damage to organizations they are against.
- Internal Users: This can be either an (ex-)employee trying to steal or break anything on purpose or internal users making mistakes, however, having a significant impact.
- Script-kiddies: amateur “hackers” trying to gain access by “downloadable” scripts or applications.
To deeply apprehend the threat actors and their techniques that we’re facing from these enemies, we can distinguish three types of Threat Intelligence Data[3]:
- Tactical: This intelligence focus on the tactics being used. These so-called TTPs (Tactics, Techniques, and Procedures) of the actors can be found in research groups from the different security providers, like Palo Alto’s UNIT42, or threat research groups such as Group-IB. This type of information aims to determine whether configurations in certain technologies need adjustments or additional measures need to be taken. The biggest downside of this that this type of information is scattered in multiple sources and hard to aggregate on threat and relevance for your specific environment, especially if you are an individual company.
- Operational: Information about CVE’s (Common Vulnerabilities and Exposures), current attacks, etc., that are used to, e.g., monitor the present network traffic and identity vulnerable systems in the network. The goal of this type of information to prevent security incidents from actually happening on a day-to-day basis. These CVE’s are translated into a CVSS (Common Vulnerability Scoring System) score based on which follow-up actions are defined. However, this way of working has a limitation, since it only contains the known and not the unknown vulnerabilities and is often a manual process of analysis, interpretation and communication.
Also, the reliability might be limited. E.g. UNIT42 is the largest contributor, while Microsoft is far off from that. Even though a lot of vulnerabilities are still after more than 25 years in Microsoft products. However, this might be caused by the massive amount of earnings Microsoft makes on Cyber Security. In 2020, Microsoft makes more than 10 billon revenue from their security business[4], a business based on securing customers from their own Microsoft Vulnerabilities? We referred earlier to this perverse model in our blog.
A better way of gathering vulnerability information from all available sources automatically and determining the actual risk and actions in an automated way, for example via SOAR technology (Security Orchestration, Automation and Response) is a way forward but still in its infancy.
- Strategic: Information about developments in the type of threats, geopolitical changes, threat actors and their motives, capabilities, etc. The goal of this is to determine whether new threats emerge that might hit your company you should prepare for in advance.
CrowdStrike provides a stunning view per industry. They list adversaries to industry types. They also show industries you’re not a target from the state sponsored hackers, but you are a target for the (Organized) Crime.
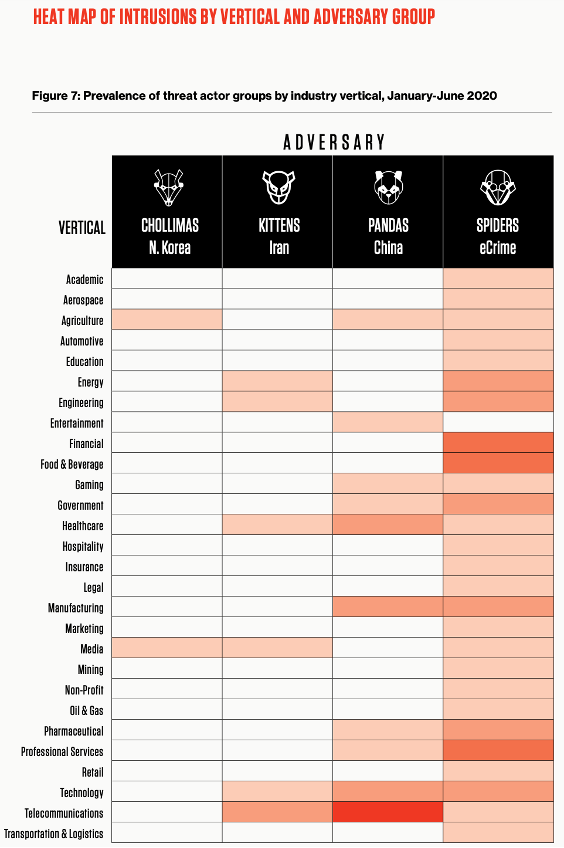
Next to what you need to do yourself, there are also initiatives of governments but also communities, like the Ransomware Task Force (RTF), consisting of a group of 19 security firms, tech companies, and non-profit organizations, that try to help all of us to understand mainly our own threat landscape. In general, however, the focus is on helping you defend your data assets against an enemy that will never stop coming at you instead of defeating the enemy.
To Really know your enemy
In addition to that famous line by Sun Tzu, which is often misquoted by stating, “To know your Enemy, you must become your Enemy”, there is a comment made to the original line the commentators in the Art of War. Chang Yu said: “Knowing the enemy enables you to take the offensive, knowing yourself enables you to stand on the defensive. The attack is the secret of defense; defense is the planning of an attack.”It would be hard to find a better epitome of the root-principle of war”. Besides, as mentioned in the introduction by Colonel David H. Hackworth, “you take fewer casualties attacking than retreating”.
Therefore, we need to do more than just defend ourselves and focus on our strengths and weaknesses to anticipate on TTPs, developments or CVEs. We need to understand the enemy’s motives and weaknesses and take the offensive route to exploit them. Like, the Dutch Intelligence Agency AIVD did by infiltrating to detect Russian State sponsored hackers Cozy Bear or APT29[5]. AIVD would have been present in their network for about 2.5 years, really learning about how they operate, where they work on, what they look like, etc. Perhaps we need more of that.
Based upon what great army leaders in history taught us is that only the defensive approach is not the right way. We need to do more and go into the offensive mode. The question however is whether we need to start counter cyber-attacks or whether it is sufficient to get into the closed hacker networks and bring them out in the open. Perhaps if we shed light on these attackers, and bring the criminals to justice. Have a meaningful conversation with State Leaders and we might be able to master this war.
[1] About face, the odyssey of an American warrior, Colonel David H. Hackworth & Julie Sherman 1989, 2020 reprint – page 15
[2] Cybersecurity in 60 minutes by Yuri Bobbert & Melvin Broersma ISBN 9789461263032
[3] Cyber Threat Intelligence Overview – ENISA Threat Landscape, From January 2019 to April 2020
[4] https://www.microsoft.com/security/blog/2021/01/27/microsoft-surpasses-10-billion-in-security-business-revenue-more-than-40-percent-year-over-year-growth/
[5] https://nos.nl/nieuwsuur/artikel/2213767-dutch-intelligence-first-to-alert-u-s-about-russian-hack-of-democratic-party.html
