Over the last seven years, our role as Chief Information Security Officer (CISO) has drastically changed. According to our Microsoft Outlook Analytics client, more than fifty percent of our mail is spam from cybersecurity suppliers, trying to grab our attention by selling fear, uncertainty and doubt (FUD). Over the last decade, we’ve seen this industry explode with self-proclaimed “cyber pros” and fuzzy vendors in the cyber domain. Is this because industry strategy agencies like IDC, Gartner, and Forrester predict that security spending keeps on increasing? Or is it because the cyber consumer just follows the herd? The latest figures indicate that an astonishing 22% of the IT budget is allocated to cyber and information security. Our own experience is that dialogues with C-level execs nowadays ask: Are we doing the right stuff, and are we doing this stuff right? How do we measure and monitor our return on security investments (ROSI)? And, where do we get the ‘biggest bang for the buck’. It’s a dialogue that very few suppliers actively participate in, while interacting with their CISO customers.
The overarching problem for today’s CISOs is to separate sense from non-sense. Non-sense being the complete wood of FUD sellers; sense being in- and oversight into the relevant issues particular to the three organizational levels.
To get more sense of what digital security needs to achieve, first the CISO needs to have the right in- and oversight into the relevant organizational issues. Therefore let’s first elaborate on three main perspectives that define the organizational scope of the CISO. These different levels require different viewpoints and attention points in the dialogue about the return on security investments. Second, to find a way through the non-sense of security software solutions and services we will address the technology under-utilization issue that companies often face. Both factors will significantly contribute to getting the ‘biggest bang for your security buck’.
Three main perspectives to define the organizational scope
Conversations at the board level
At the board level, the CISO must deliver insight and oversight into major cyber risks. This insight must be reflected from relevant infosec and risk intelligence sources inside and outside the company. Its impact on the company and its stakeholders should ideally be expressed in economic terms. But these days, the board’s responsibility goes beyond strict financial performance. Organizations need to demonstrate good governance and take sincere ownership of Corporate Social Responsibility (CSR) and associated Sustainable Development Goals (SDGs). They need to take ownership of the ‘wellbeing of the firm’. This means the CISO is also responsible for assuring the accuracy and reliability of the source data that provides insight into these, not strictly financial goals. From this perspective, it should come as no surprise that half of all C-level executives have cybersecurity issues on their board’s agenda once a quarter. Companies lacking adequate care for their data, digitization, risk, and security will end up losing the game.
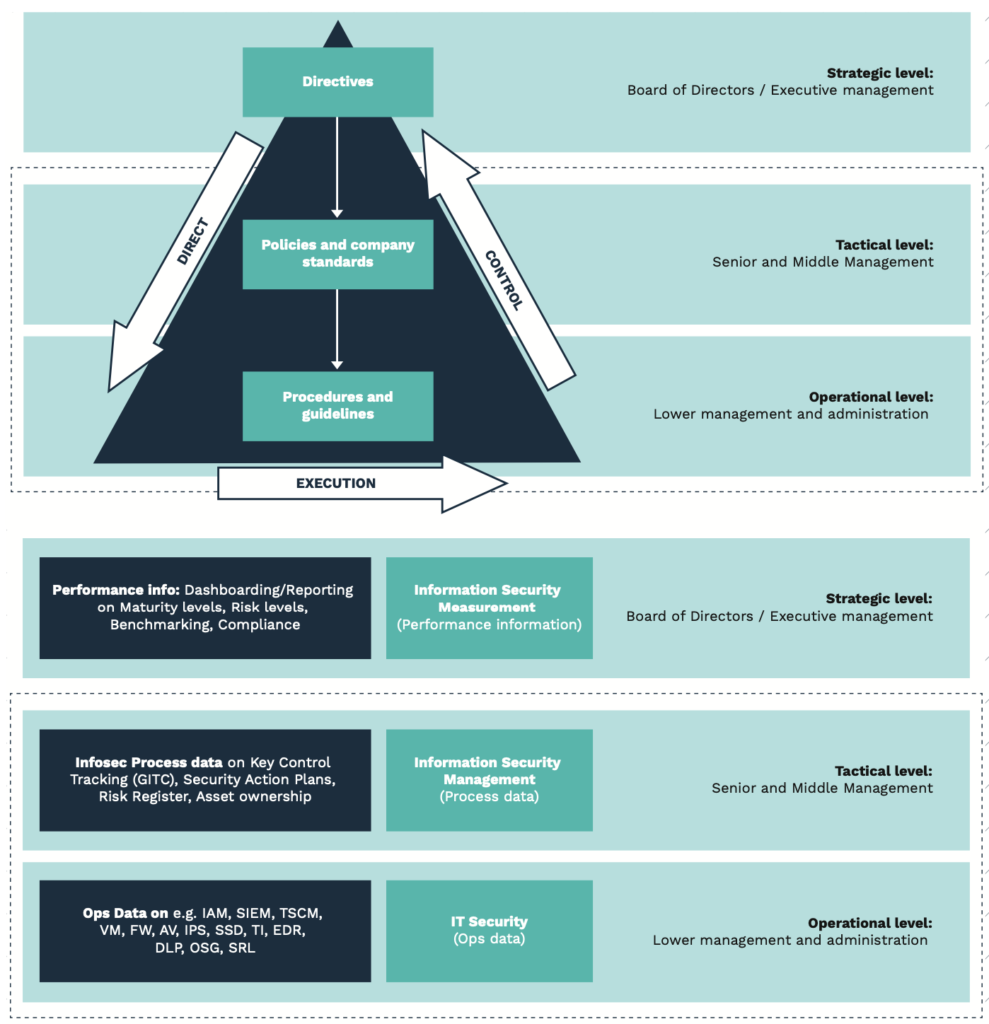
Conversations at managerial level
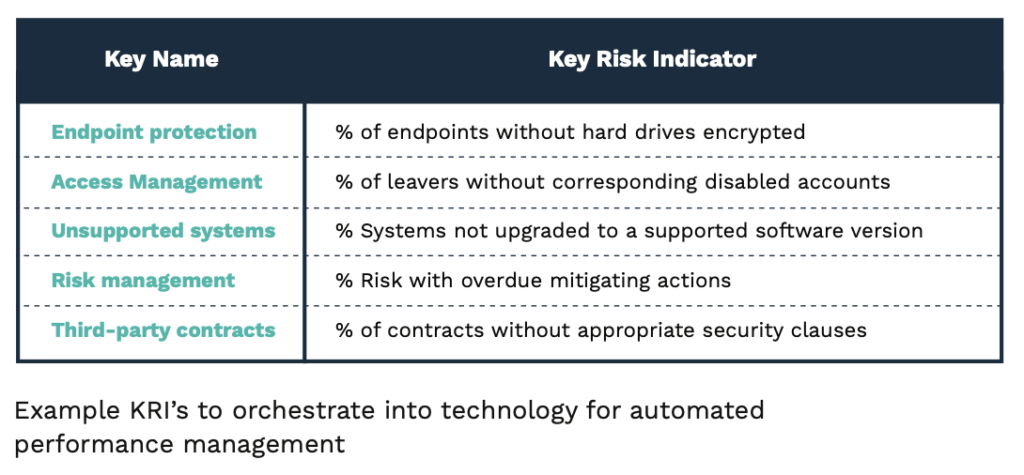
At the second (managerial) level, insight and oversight on proper risk and security ownership is relevant. The main responsibility of managers at this level is to ensure that the company’s DNA is vaccinated with sufficient security, risk awareness, ownership, leadership and craftsmanship. The CISO’s main role is that of a doctor who constantly diagnoses who needs appropriate treatment, and helps to make the right decisions, rather than being perceived as the ‘red tape general’. At this managerial level, business and asset owners need to rely on clearly predefined Key Risk and Performance Indicators (KRI/KPI) that are standardized throughout the company and orchestrated into the technology, people and processes. This sounds simple enough, but these processes require serious effort to implement in large and complex environments. They often lack the capabilities and architectural talent to translate this risk strategy into the operations. We’ve observed at first hand several companies struggling with operational security processes and technology such as micro-segmentation, security operations, and incident response.
Conversations at operational level
Implementing cybersecurity is established (e.g. designed and engineered) at the organization’s operational level. They are responsible for getting relevant and reliable infosec and risk intelligence information from sources inside and outside the company.
The operational level is the organization’s central nervous system. The main problem for all organizations with a reasonable size and technical legacy, is to dynamically align technical implementations with their internal or external requirements for cyber threats that manifest themselves quickly and unpredictably. The alignment of Governance to Management to Operations is a major struggle for many CISOs. Effective collaboration, orchestration and administration are required to reduce the stress and inaccuracy CISOs currently have to deal with.
Despite enormous progress in the industry, inaccuracy remains an enormous challenge for many organizations. This is evidenced by inadequate detection rates and slow response times to attacks. The main root causes are insufficiently configured SIEM systems, static use-cases, manual handovers, etc. But the stakes are high. An inadequate and seemingly weak response to breaches can trigger a negative impact on the company’s perceived value and potentially of its share price. This information rarely trickles down to operational teams.
The complexity of alignment issues emphasizes the necessity for further end-to-end architecting and orchestrating of security policies into technology of, for example, Cloud Access Security Brokers (CASB), Information Security Management Systems (ISMS), SOC’s, End Points, Pipelines, Containers and further automation of the controls and their proof of effectiveness to demonstrate proper assurance to the top.
We firmly believe that– according to a recent report by Wakefield Research and Deloitte – this is the main reason why half of the CISOs want to outsource their SOC and get more ‘bang for their buck’.
Technology under- or mis-utilisation
In a previous publication we reported that 50% of the implemented technology is not configured and maintained adequately. Half of the respondents in the mid market segment (100-5000 fte) recognised this as a concern but also as an opportunity. This means that companies can leverage more on existing installed base than they currently do. This also means that companies can also gain more financial benefit from their current investments. Experience learns that nowaday we need to deal with three dilemmas. 1.) Information asymmetry, 2.) attack complexity and 3.) lack of validation-feedback-loops on the performance of security technology.
Information asymmetry
Information asymmetry is the phenomena we already touched upon in our previous blog (Akerlof). It is also known as “information failure,” and occurs when one party to an economic transaction possesses greater material knowledge than the other party. This typically manifests when the seller of a good or service possesses greater knowledge than the buyer; however, the reverse dynamic is also possible. Almost all economic transactions involve information asymmetries. This means that the buyer and the seller are not in sync on what the product can, should or must do. Most of the time resulting in disappointments because the customer is not happy, since he/she expected more outcome to support a process or solve an issue. And the seller is not happy since he is squeezed for a low price while he wants to deliver appels but they squeezed him in the procurement process so far he is forced to deliver a sour lemon. The sour lemon being only the product with default settings. Downside of this is that, the bought security product, only a small part of the functions is used in practice. Not because the seller doesn’t want to deliver it but because the end user doesn’t know exactly what he wants and/or the product exactly can do. Did you know that an organisation uses an average of 70 security tools? And that 50% of the IT investments is not substantiated with a proper business case1?Later on more about that.
Attack complexity
Attack complexity is the phenomena of the huge increase in unique malware variants being used in more sophisticated and automated attacks. High volumetric attacks fire-hosed at our corporates, ultimately resulting in large amounts of events. Events that Security Operations Centre struggle with to collect, interpretate, analyse and response to. Traditional SIEM systems are not equipped to deal with this either since they only alert on known “use-cases”. With annual count of 1 bilion unique malwares this struggle cannot be dealt with by human hands but require automated orchestration and response systems.
Validation of security controls
Validation of security controls on a continuous basis is a must since keeping up the pace of the cyber-complexity mentioned above you simply cannot afford to “drop the ball”. In daily practice we see companies failing to test their controls, not test at all and have a culture of sloppiness (Waternet). Dropping the ball and getting sloppy means that in the end you pose a risk. You cannot explain what happend to you after a hack and simply cannot determine what type of data was stolen. The more time you need to publicly explain the more risk you pose of burning financial value. Like Altran, RSA, Sony and ING in 2013. Thus realtime security control validation and feeding back the performance data is a must to gain oversight and control. But are organisations up to this? We just learned that 35 security tools are bought without proper scrutiny, implemented with half of its functionality and are rarely validated.
Good practice here is to assess the fitness of existing technology and start a fitness program for your security technology. Quantification of cyber-risks versus the cost of the control reveals the ROSI per control, and the “ROSI as a whole”. By applying these methods it is possible to gain more bang for your security buck.
Future capabilities of the new Cyberleader
We see the role of the CISO expanding to ‘economist’, ‘talent magnet’ and ‘orchestrator’ with a clear vision of how to address the pitfalls at the three organizational levels.
Economist because the CISO needs to rely on detailed, reliable source data to determine the cyber risk level in the context of all other risks and be able to clearly present the benefits gained from the costs made. The CISO needs to explicate and sell the board the ‘biggest bang for the security buck’, based on facts and figures.
Talent magnet because of the ongoing ‘war’ on security talent that anchors risk and security leadership, craftsmanship and ownership to continuously ‘sharpening the saw’ and streamlining the operation; and finally, to demonstrate reasonable assurance over the Information and Cybersecurity function from bottom to top. This means the CISO needs to lead and influence the hiring process of top-notch staff that are capable of vaccinating
and positively influencing risk and security owners, talent that is capable of engineering KRIs and KPI mechanisms into the technology and processes, but also professionals that know when enough is enough, know the capabilities of current and new tooling and can make a good judgement when new FUD sellers are actually welcome or not.
Orchestrator because ‘third- party risks’ are the biggest risk for platform-based business models working in a large eco-api-based-system that require clear, predefined indicators to monitor the cyber performance over multiple environments (from left to right). This means that the CISO needs architect and orchestrate the security of the entire chain, so that he or she gains full visibility on the effectiveness of the security controls.
By effectively addressing these roles, you can have relevant conversations with all stakeholders, regardless of the organizational level at which you are interacting or the topics you address, such as ROSI, orchestration, streamlining SOC processes or outsourcing security. Suppliers that can contribute to the dialogue about where to gain the biggest ‘bang for the buck’ will be those who will win the customers’ hearts.
- Dr. Kim Maes examined (at Antwerp Management School) the use of Business Cases in IT. We adopted his checklist in our book for setting up the Business Case as well as reviewing it.
