Analyzing Business Information Security for a data breach use case
In a digital business world that is highly distributed via an eco-system, ensuring your digital assurance becomes vital. Everything needs to continuously work and Confidentially, Integrity and Auditability have to be assured, especially when your business is regulated and should demonstrate to be “in control”. Nevertheless, how do we do that when business models are under fire by hackers? Hackers using heavily automated attack methods and work as well in a distributed evasive platform-model that disguise their identity and criminal organization. Therefore, hackers form a threat to your business. Varying from State sponsored hackers to scriptkiddies all finding sophisticated ways to hammer on your front porch of your business. To you an IP address means your API store or critical business process; for a hacker it is just an IP number attack not caring and knowing the impact.
As business leaders, we need to question ourselves:
- How can we as business managers distinguish diverse type of hackers and their intention?
- How can we simulate scenarios and calculate the impact on the business in terms of economic loss?
- What can we do to identify, protect and respond to that and which security investments are justified to mitigate the risks?
These are typical questions a CISO needs to master in a world where money is made via digital business platforms and the role of the CISO is to take leadership and ownership. This is exactly where we guide tech leaders of the future on when following the Cybersecurity master program. Periodically we examine cases students executed as part of assignments and shed new light or fresh insights on the topic. This time we ask Pascal de Haan (DSM) and Tim Vandeput (TConsult) on analyzing BIS and the potential impact of a data breach at a financial company.
1. What problem did you investigate?
We investigated the potential impact of a vulnerability in the digital channels of a financial institution. Financial players are more and more reliant on digital interaction with their customers and partners, partly triggered by new regulations, which require banks and other financial organizations to expose their services via API’s.
The additional introduction of DevOps also leads to more frequent updates and more frequent releases of functionality in the digital channels and, hence, increases the likelihood of vulnerabilities in code being released as well. In this scenario, we assumed such a vulnerability to allow less honorable persons to extract customer records, including personal information from the core systems. With more than 3 million active customers, this could result in significant financial and non-financial damages to the case company.
2. How did you do this? What was your approach to this?
We started our research assignment by looking at the company’s annual report, press releases and other publicly available information, as well as internal documents, to obtain a view on its current strategy and risk governance. Then we conducted an interview with the organizations’ head of IT Security. This was necessary to gather data for the next steps where we performed a data breach tangible and intangible cost analysis and resulting gap analysis using reference data from IBM Ponemon and Verizon DBIR. The visual below demonstrates the several attack vectors we have investigated as viable scenarios. Not just for our case but they could be relevant for any financial company.
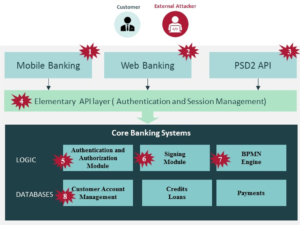
We then proposed security mitigation activities with alternatives and performed a Return on Security Investment (ROSI) calculation to demonstrate that the investments are justified. Finally, we linked everything together through a Cybersecurity Balanced Scorecard (BSC) and accompanying roadmap that show how these investments in cybersecurity support the organizations strategy. A nice exercise was the CISO assessment which compared the type of CISO the case company has now, compared to what is recommended based on the CISO Assessment Level Model (CALM) by Russel Reynolds.
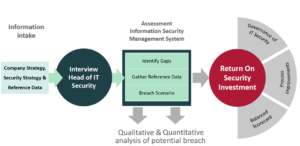
3. What did you find? What should people really know?
The potential financial impact (tangible and non-tangible) exceeded all expectations. By doing the exercise with the case company, we created awareness of the potential consequences.
By making the potential costs as transparent as possible, it helps to “sell” the investment to senior management and boards.
By using this financial impact in the Return of Security Investment (ROSI) calculation method, we were able to justify the security investment.
Return on Security Investment represents the amount of risk reduced, less the amount of money spent, divided by the amount spent on cybersecurity controls. The business would like to know how much they should spend on security to reduce the risk and when the investment has the largest return. The goal of the ROSI is how much the business can save by investing in IT security. Parallel to that, look at all cybersecurity investments and prioritize the investment portfolio.
However, before we can do a ROSI calculation we need some information. We have conducted a Business Impact Analysis (BIA) first to identify the critical business functions and associated assets. This starts with figuring out which processes are critical for the company’s success. Another important perspective for an organization derives from analytical risk exposure methods that explain the cost of security incidents. We take the Single Loss Exposure (SLE) and multiply it by the Annual Rate of Occurrence (ARO) and the result of this is the Annual Loss Exposure (ALE). ALE = ARO x SLE
To do the actual ROSI calculation you need these parameters:
- Single Loss Expectancy (SLE) = the expected amount of money lost during a single security incident.
- Annual Rate of Occurrence (ARO) = the probability of a security incident occurring in a year.
- Annual Loss Exposure (ALE): The total annual financial loss expected from a security incident.
- Recurring Security Costs (RSC) = Annual security costs (licenses, audits, specialized staff).
- Mitigation Ratio = Percentage of threats deterred by the security solution.
- Security Cost (Scost) = Initial investment in the digital security measure
Examples of potential costs that we anticipated are (see table for complete overview):
- GDPR (fines) (blue)
- Investigations and forensics (olive green)
- Victim reimbursements (wheat)
- Diminished market share (orange)
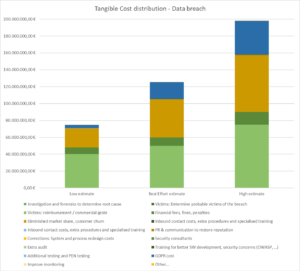

In this example calculation:
- ALE: €200.000.000
- Risk Mitigation: 50% by adopting a security measure
- Scost: €0.5 million
- ROSI: 1900%
Due to the large ROSI value of 1900%, additional costs can be increased up to 99 million € before the ROSI becomes negative.
Best effort ROSI: 900%, additional costs can be increased up to 49 million before ROSI becomes negative.
Low estimate ROSI: 560%, additional costs can be increased up to 34 million before ROSI becomes negative.
The following improvement areas were found to further reduce the risk:
- Internal Risk Management Scoring and mapping of risks to internal controls
- Lack of security embedded within the new DevOps and agile methodology processes
- Improvements in the three lines of defense model
- Shift towards a more pro-active approach for risk monitoring
- Improve independent monitoring of the efficiency of the implemented controls
As you might have noted above, we found process and governance improvements instead of hard controls. A good aligned end-to-end process, which utilizes the three lines of defense model, was not in place within the case company. By utilizing the three lines of defense model and improving the governance and processes, it ensures (effective) controls are implemented and ineffective controls are observed timely. By making that with a Balanced Scorecard, it resonates more with the board of the case company.
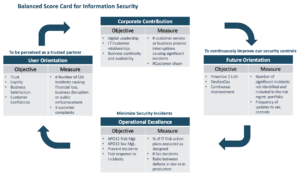
4. Why does this matter? / What can others learn from your case?
By making the potential costs transparent and using it in the ROSI calculation you make it tangible for the company what you try to protect with your investment. This makes it “easier to sell” it to the board to get the investment approved.
We also observed having a good governance and process in place should ensure continuous improvement and the lines of defense should strengthen the controls on a continuous bases. If these mechanisms are in place, you are creating a self-learning and validating organization.
5. Why do you advise others to follow such a course/master program?
We would advise doing a masters course/program to get insights in exciting theoretical models, applying these in practice, reflect on it along the way with your case company, your peer students and professors, all leading to growing as a professional, while giving a practical and applicable advise to your case company.
Conclusion by prof. dr. Yuri Bobbert
In conclusion, we can state that analyzing several cyber actors towards the organizations is needed. Not only via traditional ways such as likelihood and impact but also in a more economic and quantifiable way. By doing the analysis based upon known actors, (such as state sponsored hacks with espionage and economic benefit intent, most of the time derived from threat reports from countries -such as the Belgium or Dutch National Cyber Security Centers (NCSC). Where each country identifies relevant actors and their ways operating in certain sectors. Combining this type of threat data with business specific loss data, helps organizations identify threat scenarios, potential breach occurrence (translated in the ALE) and potential financial impact. You can provide direct insight into the cost for the business and the potential returns by viewing the individual risk-impact-treatment scenarios and the sum of all the risk-impact-treatment scenarios as a whole and then map those scenarios on running security activities as well as on new security activities and the associated spend. Monitoring the individual initiatives and the overall program via Balanced Score Cards methodologies helps with better buy-in at senior business management and boards. These are methods, techniques and soft skills that AMS provide to potential security leaders that follow the Executive master program.
